In OSPF, we can have an area that is not directly connected to the backbone area by using the virtual link feature. If somehow, OSPF authentication is enabled in area 0. Routers that is connected through a virtual link must have the authentication configured too. This is because the router believe that it is directly connected to the area 0, and since routers in area 0 authenticate themselves for communicating, the virtual-linked router would no longer able to communicate with the routers in area 0.
The command to configure authentication on a virtual-link is:
area NUMBER virtual-link A.B.C.D message-digest-key NUMBER2 md5 WORD
NUMBER: the area number where both virtual-linked routers reside.
A.B.C.D: the router-id of the peer router.
NUMBER2: the id number of the digest key.
WORD: the authentication password used.
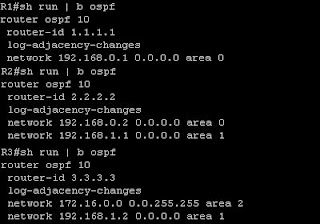
So, let's say that we have this topology

We have an md5 authentication configured in area 0 with password of "cisco". To configure this authentication for area 0, go to all router in area 0, which in this case are R1 and R2 and type the following command (assume that you are from the global configuration level and the OSPF process id is 1):
router ospf 1
area 0 authentication message-digest
interface fastethernet1/0
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco
Now, since authentication is in place for area 0, in order for area 2 to have connectivity with the rest of OSPF network, the authentication should be configured on the virtual-linked routers too, which in this case are R2 and R3. We first go to R2 and go to its OSPF process 1 configuration level and enter the following command
area 1 virtual-link 3.3.3.3 message-digest-key 1 md5 cisco
Next we go to R3, go to the OSPF process 1 configuration level and enter the command:
area 1 virtual-link 2.2.2.2 message-digest-key 1 md5 cisco
area 0 authentication message-digest
We need to configure the command "area 0 authentication message-digest" on R3 to avoid authentication type mismatch error (Type 0 - Null authentication on R3, and Type 2 - Message Digest authentication on R2). This is because a virtual-link is a tunnel that makes as if R3 is directly connected to area 0, and since area 0 is configured with message-digest authentication, therefore R3 should be configured to use message-digest authentication too on area 0.